Tcpdump & wireshark
命令行查看当前机器公网ip¶
检测机器端口开放¶
# 网页服务直接下载检查内容
wget 4.shaojiemike.top:28096
# -z 选项指示 nc 仅扫描打开的端口,而不发送任何数据,并且 -v 用于获取更多详细信息。
nc -z -v 4.shaojiemike.top 28096
# IPV6 也行
$ nmap -6 -p 8096 2001:da8:d800:611:5464:f7ab:9560:a646
Starting Nmap 7.80 ( https://nmap.org ) at 2023-01-04 19:33 CST
Nmap scan report for 2001:da8:d800:611:5464:f7ab:9560:a646
Host is up (0.00099s latency).
PORT STATE SERVICE
8096/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
$ nmap -p 28096 4.shaojiemike.top
Starting Nmap 7.80 ( https://nmap.org ) at 2023-01-04 19:19 CST
Nmap scan report for 4.shaojiemike.top (114.214.181.97)
Host is up (0.0011s latency).
PORT STATE SERVICE
28096/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
wireshark¶
显示过滤¶
上方的过滤窗口
tcp.port==80&&(ip.dst==192.168.1.2||ip.dst==192.168.1.3)
ip.addr ==192.168.1.1 //显示所有目标或源地址是192.168.1.1的数据包
eth.addr== 80:f6:2e:ce:3f:00 //根据MAC地址过滤,详见“wireshark过滤MAC地址/物理地址”
tcp.port==23
捕捉过滤¶
抓包前在capture option中设置,仅捕获符合条件的包,可以避免产生较大的捕获文件和内存占用,但不能完整的复现测试时的网络环境。
host 192.168.1.1 //抓取192.168.1.1 收到和发出的所有数据包
src host 192.168.1.1 //源地址,192.168.1.1发出的所有数据包
dst host 192.168.1.1 //目标地址,192.168.1.1收到的所有数据包
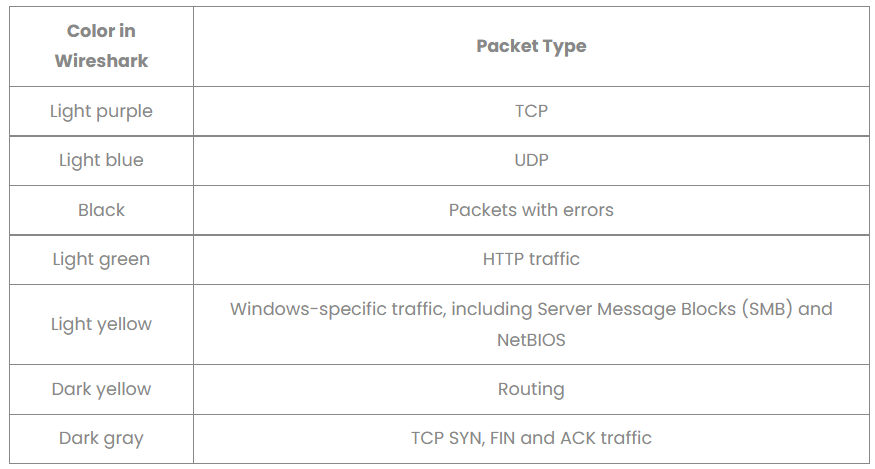
color 含义¶
tcpdump¶
传统命令行抓包工具
常用参数¶
注意过滤规则间的and
-nn:- 单个 n 表示不解析域名,直接显示 IP;
- 两个 n 表示不解析域名和端口。
- 方便查看 IP 和端口号,
- 不需要域名解析会非常高效。
-i指定网卡-D查看网卡-v,-vv和-vvv来显示更多的详细信息port 80抓取 80 端口上的流量,通常是 HTTP。在前面加src,dst限定词tcpudmp -i eth0 -n arp host 192.168.199抓取192.168.199.* 网段的arp协议包,arp可以换为tcp,udp等。-A,-X,-xx会逐渐显示包内容更多信息-e: 显示数据链路层信息。- 默认情况下 tcpdump 不会显示数据链路层信息,使用 -e 选项可以显示源和目的 MAC 地址,以及 VLAN tag 信息。
输出说明¶
- ip 是 192.168.1.106,源端口是 56166,
- 目的地址是 124.192.132.54,目的端口是 80。
>符号代表数据的方向。
Flags¶
常见的三次握手 TCP 报文的 Flags:
常见用途¶
- 根据目的IP,筛选网络经过的网卡和端口
- 能抓各种协议的包比如ping,ssh
案例分析¶
github ip 为 20.205.243.166
ifconfig显示 ibs5的网卡有21TB的带宽上限,肯定是IB卡了。
sudo tcpdump -i ibs5 '((tcp) and (host 20.205.243.166))'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ibs5, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
15:53:53.848619 IP snode0.59878 > 20.205.243.166.http: Flags [S], seq 879685062, win 64128, options [mss 2004,sackOK,TS val 4096492456 ecr 0,nop,wscale 7], length 0
15:53:53.952705 IP 20.205.243.166.http > snode0.59878: Flags [S.], seq 1917452372, ack 879685063, win 65535, options [mss 1436,sackOK,TS val 1127310087 ecr 4096492456,nop,wscale 10], length 0
15:53:53.952728 IP snode0.59878 > 20.205.243.166.http: Flags [.], ack 1, win 501, options [nop,nop,TS val 4096492560 ecr 1127310087], length 0
15:53:53.953208 IP snode0.59878 > 20.205.243.166.http: Flags [P.], seq 1:79, ack 1, win 501, options [nop,nop,TS val 4096492561 ecr 1127310087], length 78: HTTP: GET / HTTP/1.1
15:53:54.058654 IP 20.205.243.166.http > snode0.59878: Flags [P.], seq 1:89, ack 79, win 64, options [nop,nop,TS val 1127310193 ecr 4096492561], length 88: HTTP: HTTP/1.1 301 Moved Permanently
15:53:54.058668 IP snode0.59878 > 20.205.243.166.http: Flags [.], ack 89, win 501, options [nop,nop,TS val 4096492666 ecr 1127310193], length 0
15:53:54.059092 IP snode0.59878 > 20.205.243.166.http: Flags [F.], seq 79, ack 89, win 501, options [nop,nop,TS val 4096492667 ecr 1127310193], length 0
15:53:54.162608 IP 20.205.243.166.http > snode0.59878: Flags [F.], seq 89, ack 80, win 64, options [nop,nop,TS val 1127310297 ecr 4096492667], length 0
$ sudo tcpdump -i ibs5 -nn -vvv -e '((port 80) and (tcp) and (host 20.205.243.166))' tcpdump: listening on ibs5, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
16:09:38.743478 Out ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 15215, offset 0, flags [DF], proto TCP (6), length 60)
10.1.13.50.38376 > 20.205.243.166.80: Flags [S], cksum 0x1fd5 (incorrect -> 0x98b6), seq 1489092902, win 64128, options [mss 2004,sackOK,TS val 4097437351 ecr 0,nop,wscale 7], length 0
16:09:38.848164 In ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 48, id 0, offset 0, flags [DF], proto TCP (6), length 60)
20.205.243.166.80 > 10.1.13.50.38376: Flags [S.], cksum 0x69ba (correct), seq 3753100548, ack 1489092903, win 65535, options [mss 1436,sackOK,TS val 3712395681 ecr 4097437351,nop,wscale 10], length 0
16:09:38.848212 Out ethertype IPv4 (0x0800), length 68: (tos 0x0, ttl 64, id 15216, offset 0, flags [DF], proto TCP (6), length 52)
10.1.13.50.38376 > 20.205.243.166.80: Flags [.], cksum 0x1fcd (incorrect -> 0x9613), seq 1, ack 1, win 501, options [nop,nop,TS val 4097437456 ecr 3712395681], length 0
16:09:38.848318 Out ethertype IPv4 (0x0800), length 146: (tos 0x0, ttl 64, id 15217, offset 0, flags [DF], proto TCP (6), length 130)
10.1.13.50.38376 > 20.205.243.166.80: Flags [P.], cksum 0x201b (incorrect -> 0x9f0a), seq 1:79, ack 1, win 501, options [nop,nop,TS val 4097437456 ecr 3712395681], length 78: HTTP, length: 78
GET / HTTP/1.1
Host: www.github.com
User-Agent: curl/7.68.0
Accept: */*
16:09:38.954152 In ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 48, id 45056, offset 0, flags [DF], proto TCP (6), length 140)
20.205.243.166.80 > 10.1.13.50.38376: Flags [P.], cksum 0x024d (correct), seq 1:89, ack 79, win 64, options [nop,nop,TS val 3712395786 ecr 4097437456], length 88: HTTP, length: 88
HTTP/1.1 301 Moved Permanently
Content-Length: 0
Location: https://www.github.com/
16:09:38.954207 Out ethertype IPv4 (0x0800), length 68: (tos 0x0, ttl 64, id 15218, offset 0, flags [DF], proto TCP (6), length 52)
10.1.13.50.38376 > 20.205.243.166.80: Flags [.], cksum 0x1fcd (incorrect -> 0x949a), seq 79, ack 89, win 501, options [nop,nop,TS val 4097437562 ecr 3712395786], length 0
16:09:38.954884 Out ethertype IPv4 (0x0800), length 68: (tos 0x0, ttl 64, id 15219, offset 0, flags [DF], proto TCP (6), length 52)
10.1.13.50.38376 > 20.205.243.166.80: Flags [F.], cksum 0x1fcd (incorrect -> 0x9498), seq 79, ack 89, win 501, options [nop,nop,TS val 4097437563 ecr 3712395786], length 0
16:09:39.060177 In ethertype IPv4 (0x0800), length 68: (tos 0x0, ttl 48, id 45057, offset 0, flags [DF], proto TCP (6), length 52)
20.205.243.166.80 > 10.1.13.50.38376: Flags [F.], cksum 0x95e2 (correct), seq 89, ack 80, win 64, options [nop,nop,TS val 3712395892 ecr 4097437563], length 0
16:09:39.060221 Out ethertype IPv4 (0x0800), length 68: (tos 0x0, ttl 64, id 15220, offset 0, flags [DF], proto TCP (6), length 52)
10.1.13.50.38376 > 20.205.243.166.80: Flags [.], cksum 0x1fcd (incorrect -> 0x93c4), seq 80, ack 90, win 501, options [nop,nop,TS val 4097437668 ecr 3712395892], length 0
16:09:46.177269 Out ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 38621, offset 0, flags [DF], proto TCP (6), length 60)
snode0 ip 是 10.1.13.50
traceroute¶
mtr = traceroute+ping
$ traceroute www.baid.com
traceroute to www.baidu.com (182.61.200.6), 30 hops max, 60 byte packets
1 acsa-nfs (10.1.13.1) 0.179 ms 0.180 ms 0.147 ms
2 192.168.252.1 (192.168.252.1) 2.016 ms 1.954 ms 1.956 ms
3 202.38.75.254 (202.38.75.254) 4.942 ms 3.941 ms 4.866 ms
traceroute命令用于显示数据包到主机间的路径。
NETWORKMANAGER 管理¶
# shaojiemike @ snode0 in /etc/NetworkManager [16:49:55]
$ nmcli general status
STATE CONNECTIVITY WIFI-HW WIFI WWAN-HW WWAN
disconnected unknown enabled enabled enabled enabled
# shaojiemike @ snode0 in /etc/NetworkManager [16:50:40]
$ nmcli connection show
NAME UUID TYPE DEVICE
InfiniBand connection 1 7edf4eea-0591-48ba-868a-e66e8cb720ce infiniband --
好像之前使用过的样子。
# shaojiemike @ snode0 in /etc/NetworkManager [16:56:36] C:127
$ service network-manager status
● NetworkManager.service - Network Manager
Loaded: loaded (/lib/systemd/system/NetworkManager.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2022-03-14 11:52:06 CST; 1 months 10 days ago
Docs: man:NetworkManager(8)
Main PID: 1339 (NetworkManager)
Tasks: 3 (limit: 154500)
Memory: 12.0M
CGroup: /system.slice/NetworkManager.service
└─1339 /usr/sbin/NetworkManager --no-daemon
Warning: some journal files were not opened due to insufficient permissions.
应该是这个 Secure site-to-site connection with Linux IPsec VPN 来设置的
需要进一步的研究学习¶
暂无
遇到的问题¶
暂无
开题缘由、总结、反思、吐槽~~¶
FJW说所有网络都是通过NFS一起出去的
参考文献¶
无